
Top Predicted Cyber Attacks of 2020 – Part 2
Just like in the past couple of years, ransomware attacks will still be prevalent in 2020, but it is predicted that not only will the attacks become more sophisticated, they will begin deploying 2 stages of extortion.
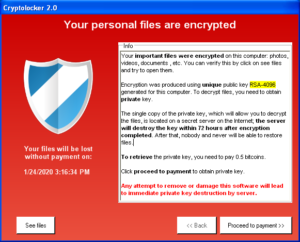
Most ransomware attacks follow a basic pattern; reconnaissance, where the hackers learn about the company, employees, controls and processes. Penetration is the next phase; this is where hackers gain access to their target. The 3rd step is fortification, when the attackers hide the evidence that they have gained access and will even go as far as protecting the devices they have attacked so other hackers can’t gain access. The next step to deploying ransomware is infiltration. This is where they perform internal reconnaissance trying to find higher value targets and acquire administration level passwords. Spoliation follows infiltration, when they will alter backups, remove some data but leave the containers, and then introduce flaws into software to make it harder to backup. The last step is the actual ransom, this is when the data is encrypted, and archives are wiped. After the ransom demand is made businesses are not left with many choices. Usually when the payment is made the hackers will pass on the encryption code and the company will be able to get back their lost data. In most attacks, this is where the transaction ends, the hackers have their money and the company has their data. In the future, the large worry is that a single stage attack will morph into a two-stage attack. In a two-stage attack, the hackers also keep a copy of all the data, eventually asking for another ransom. This time, they will threaten to leak all the personally identifiable information that is stored within the network. This second stage can be just as damaging to a company as the first stage.
Application Programming Interfaces (APIs)
Application Programming Interfaces (APIs) have been in use for years, but over the last five years they have gone from being a developmental tool to a driving force behind today’s economy. The important role that APIs play is one reason why future attacks are predicted to occur by McAfee. API’s are a set of routines, protocols, and tools for building software applications. Basically, an API specifies how software components should interact and allows different applications to speak to each other. Because they are used as a communication device between applications, there is sensitive data that is transferred through them. This data is what hackers are trying to gain access to. As more and more software and web-based applications utilize this means of communication, more entry points are created for possible infiltration and exposure. Sensitive data attacks are what is most reported on by the media, but this is not the only type of exposure that is left vulnerable by insecure APIs.
Application containerization
Application containerization has increased in popularity recently because it allows developers to create and deploy applications faster and without deploying as many resources as have been used traditionally. It is an Operating System (OS) level virtualization method used to deploy and then run applications without launching an entire Virtual Machine (VM) for each application. They share resources with the core OS, and this leads to gains in efficiency for memory, CPU and storage in comparison to conventional VM’s and physical hosting. Where the concern lays deploying containerized applications is, they are not isolated from the main OS. This allows easier access once penetrated to the entire system. They are not as easily secured as a traditionally hosted application and tools to scan and monitor the container are almost nonexistent. Because they are not as easily secured, scanned or monitored, once they have been penetrated, it is very difficult to detect the unauthorized access.
If you missed Part 1 of this series: Top Predicted Cyber Attacks of 2020
If you are worried that your data could be breached or accessed, please reach out to HubWise Technology, jmoen@hubwisetech.com (402) 210-7138 to discuss what you are currently doing to secure your network and how it can be improved.
